New Delhi, May 15: It was coming. On March 14 this year, Microsoft released a security update which addressed the vulnerability in the 16-year-old Windows XP operating system that the hackers behind the massive ransomware attack exploited and created havoc in 150 countries.
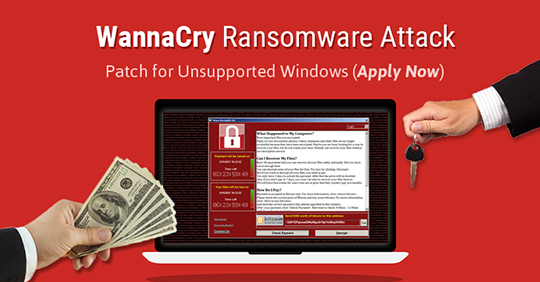
The vulnerability in the Microsoft Windows software — exploited by “WannaCrypt” — crippled computers from hospitals in Britain to police stations in India, with hackers demanding hundreds of dollars from the users for them to regain control over their data.
Once Microsoft released the patch for the vulnerability — exploited by hacker group “Shadow Brokers” after stealing a software from the US National Security Agency (NSA) — some Window XP users installed the update called “Microsoft Security Bulletin MS17-010” on their desktops and laptops.
But several didn"t.
There are nearly 150 million computers running Windows XP operation system globally. Those who didn"t pay heed to the Windows XP patch are the ones who have fallen prey to the world"s biggest ransomware attack.
Microsoft which had discontiued security updates to its out-of-date software, has also provided a security update for all customers using Windows 8 and Windows Server 2003, anticipating further attacks on these earlier platforms being used by millions.
According to the company, “customers who are running supported versions of the operating system (Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8.1, Windows Server 2012, Windows 10, Windows Server 2012 R2, Windows Server 2016) will have received the security update MS17-010 in March.
“If customers have automatic updates enabled or have installed the update, they are protected. For other customers, we encourage them to install the update as soon as possible,” said Phillip Misner, Principal Security Group Manager, Microsoft Security Response Centre, in a statement.
Meanwhile, “WannaCrypt” locked up machines, encrypted files and demanded approximately $600 in Bitcoin for a recovery key.
According to global cyber security firms, paying heed to updates can only save your data from being put to ransom.
“Install the official patch from Microsoft that closes the vulnerability used in the attack. Ensure that security solutions are switched on all nodes of the network. If Kaspersky Lab"s solution is used, ensure that it includes the "System Watcher", a behavioural proactive detection component and that it is switched on,” Altaf Halde, Managing Director of Kaspersky Lab (South Asia), told.
“Run the "Critical Area Scan" task in Kaspersky Lab"s solution to detect possible infection as soon as possible (otherwise it will be detected automatically, if not switched off, within 24 hours),” he added.
According to Subhendu Sahu, Acting Country Manager for India, FireEye, the ransomware poses high risks to organisations using potentially vulnerable Windows machines.
“We can certainly expect follow-on attacks. Organisations seeking to take risk management steps related to this campaign should install the latest Windows patches. They should also use the indicators of compromise which are associated with this activity. FireEye has also taken steps to help secure its customers,” Sahu told.
As investigators were working to track down those responsible for the ransomware attack, Microsoft President and Chief Legal Officer Brad Smith said the governments should treat this attack as a “wake-up call”.
The news led software security providers to ramp up anti-malware software.
“Upon learning of these incidents, McAfee quickly began working to analyse samples of the ransomware and develop mitigation guidance and detection updates for its customers. McAfee has subsequently provided DAT (that contain data in text or binary format) updates to all its customers and provided them and the public further analysis on the attacks,” Ian Yip, Chief Technology Officer, Asia Pacific, McAfee, told.
If you are a home Windows XP user, patch immediately follow up with an upgrade. If you are running a vulnerable system and cannot install the patch for some reason, try doing the following:
“Disable SMBv1 (a server component) with the steps documented at "Microsoft Knowledge Base Article 2696547" and as recommended previously. Consider adding a rule on your router or firewall to block incoming Server Message Block (SMB) traffic on port 445,” said a report in the technology website Engadget.
“This is big and set to get bigger. We haven"t seen anything like this since Conficker in 2008,” Amit Nath, Head of Asia Pacific-Corporate Business at cyber security firm F-Secure Corporation, told IANS.
The Conficker worm infected millions of computers including government, business and home computers in over 190 countries.
Always make sure your files are backed up.
“That way, if they become compromised in a ransomware attack, you can wipe your disk drive clean and restore the data from the backup. Using Cloud storage with anti-virus scanning abilities to share files will help users to mitigate any possible threats,” suggested Anand Ramamoorthy, Managing Director, South Asia, McAfee.
Remember this: “WannaCrypt” probably won"t work across the internet for PCs behind a firewall or router.
“But if a server is connected directly to the internet or a PC is on the same network as an infected computer, it can spread quickly — which is exactly what has happened,” the Engadget report added.





Comments
Add new comment